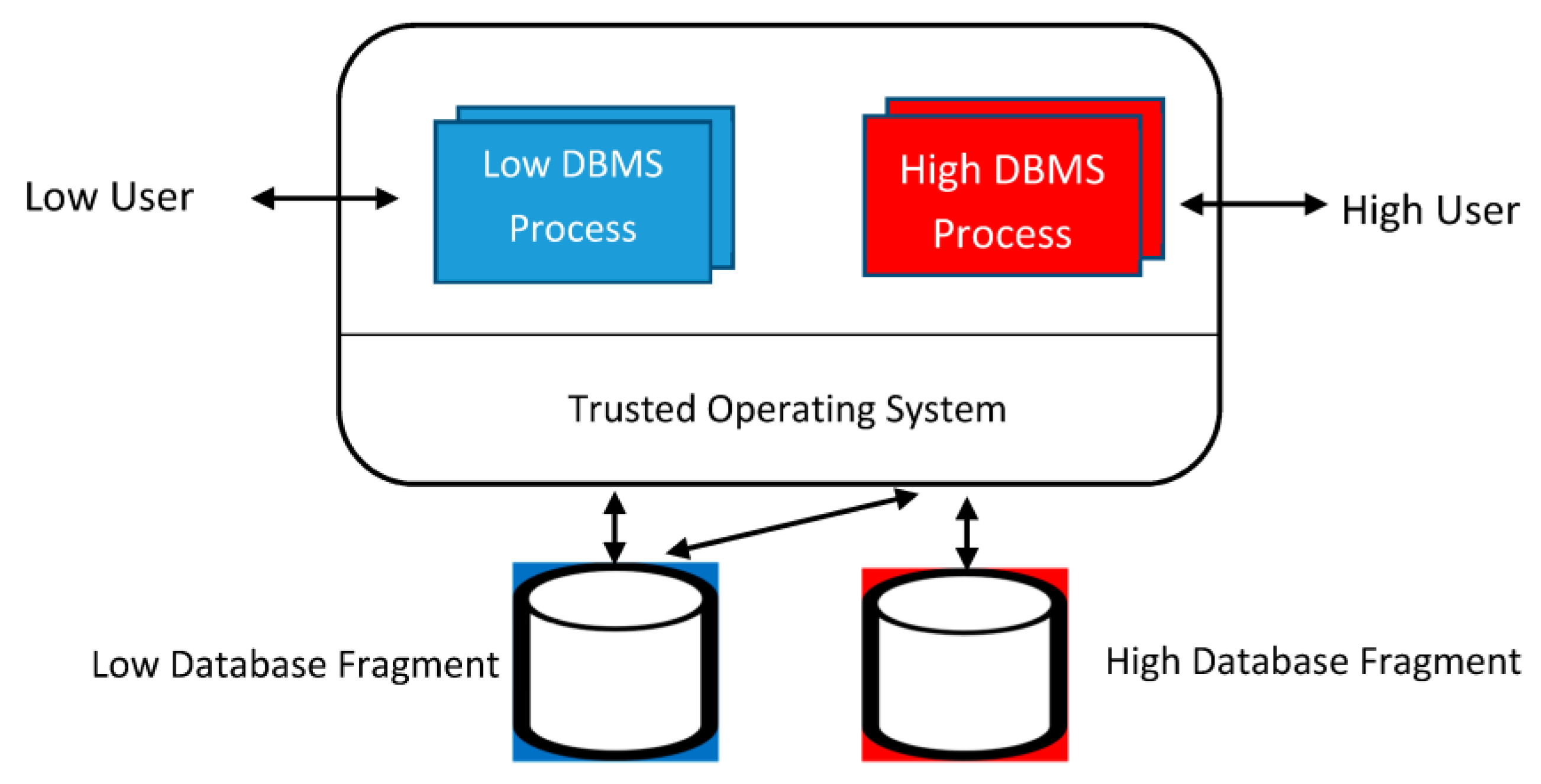
GitHub - garagakteja/Reference-Monitor-Security-Build: Restricted Python (Repy) based hands-on implementation of Security Mechanisms and Access control

The Core Concept of Access Control by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

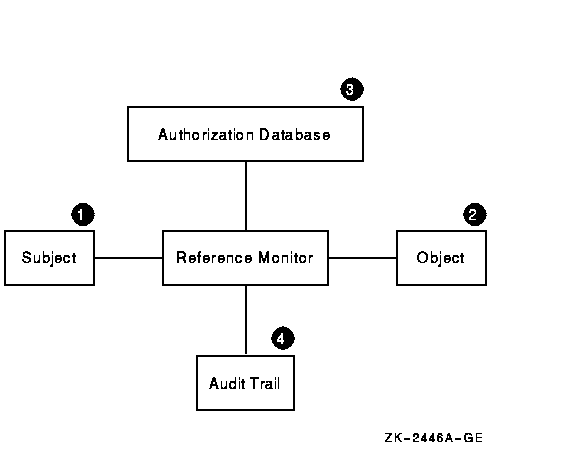
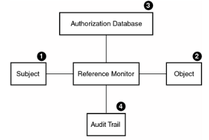
Three fundamental concepts in computer security: Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses. - ppt download

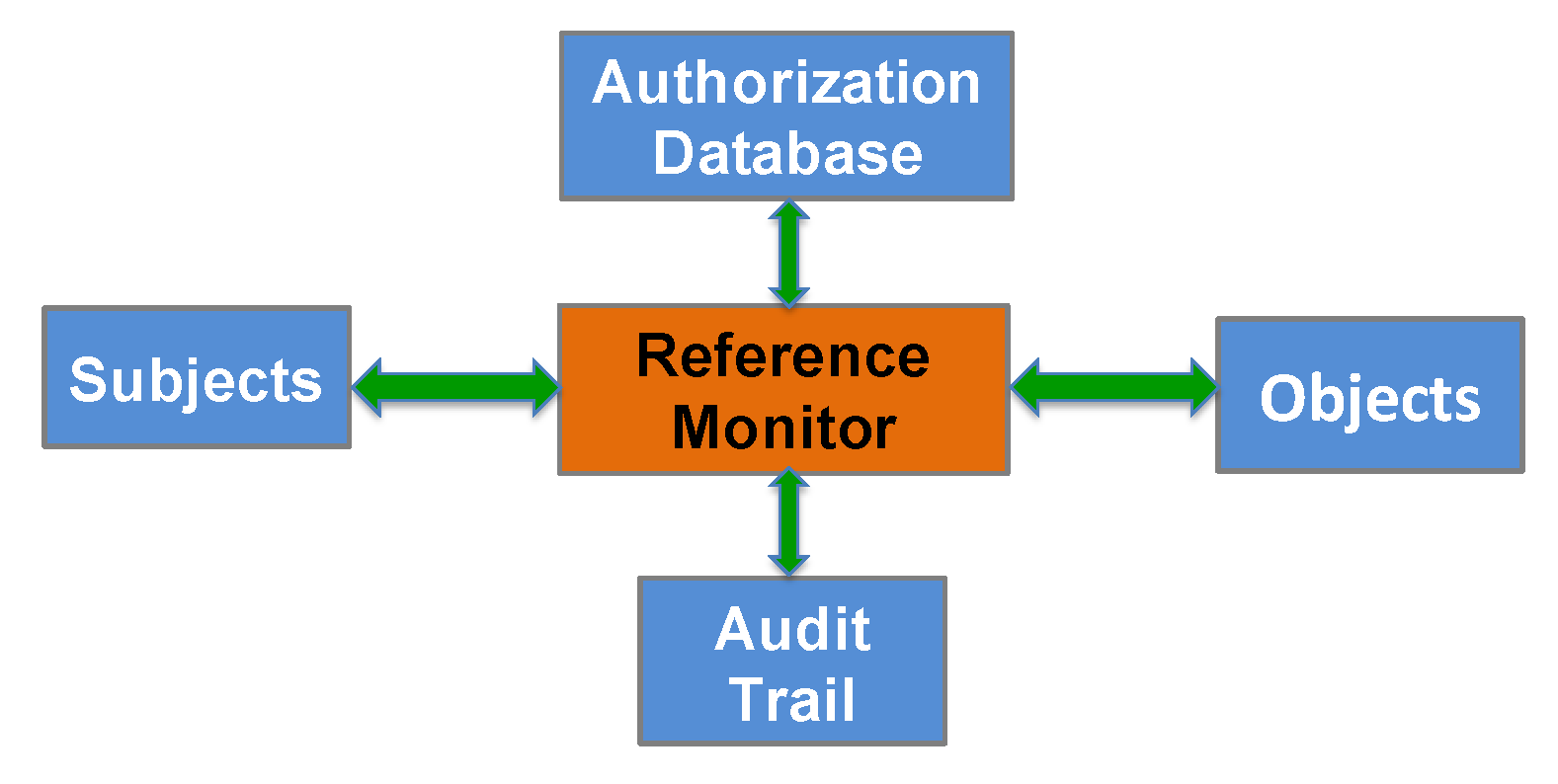

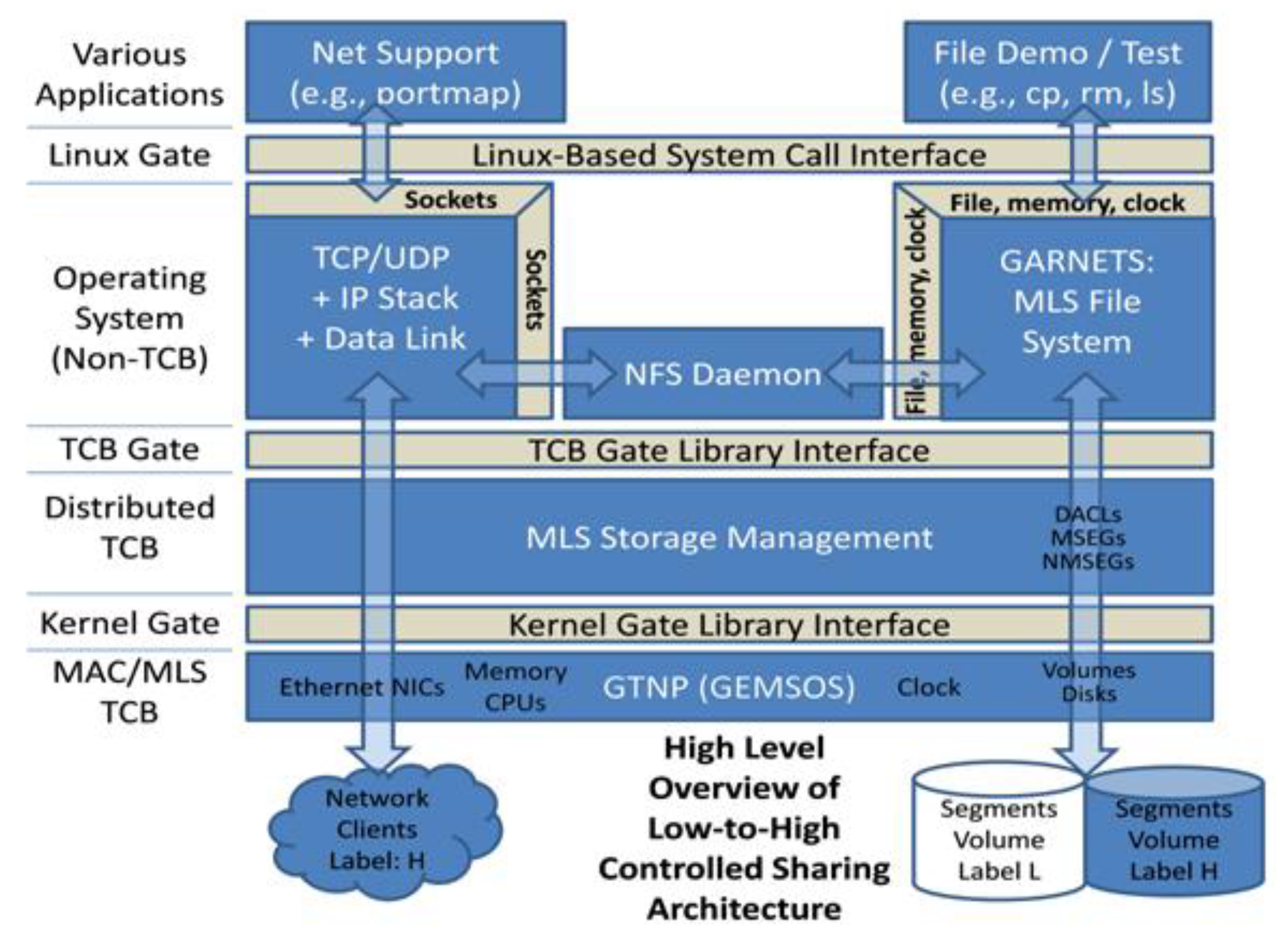
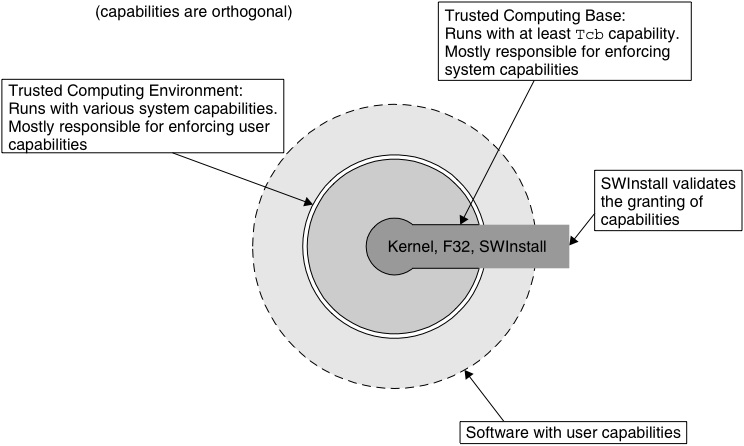

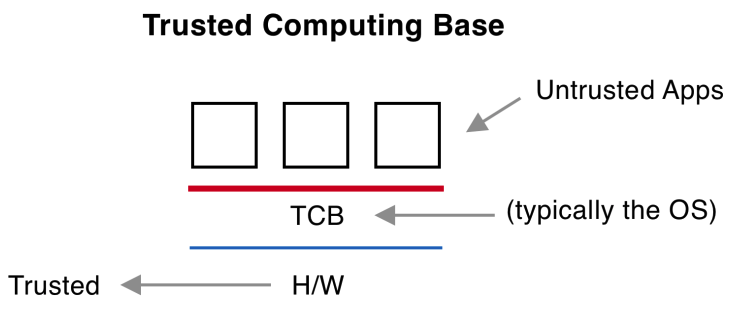

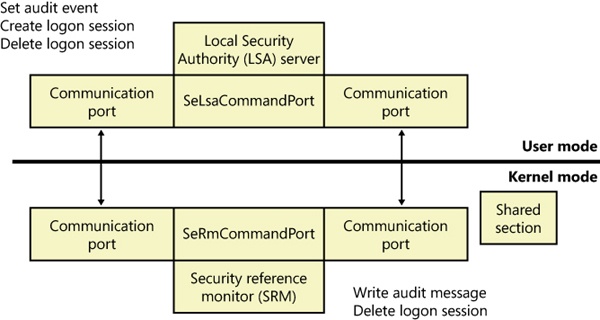



![PDF] Teaching the security mindset with reference monitors | Semantic Scholar PDF] Teaching the security mindset with reference monitors | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9733b37e5b61ccff306b21907abd3143995c1f8b/2-Figure1-1.png)