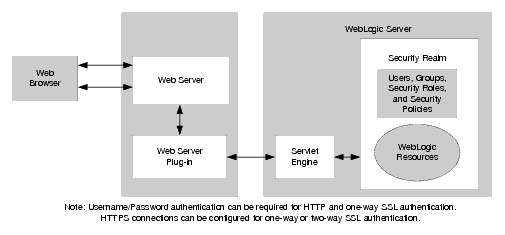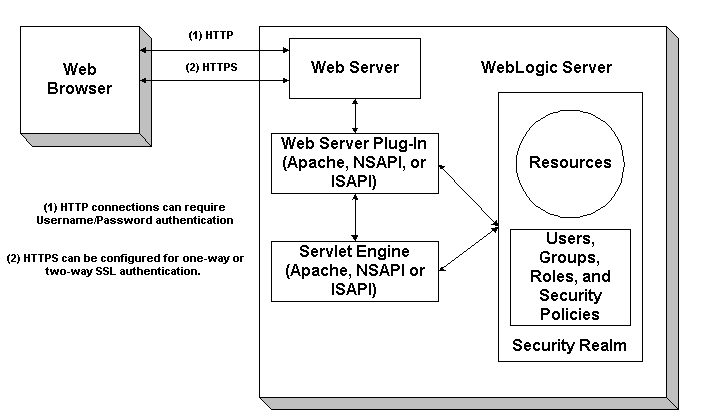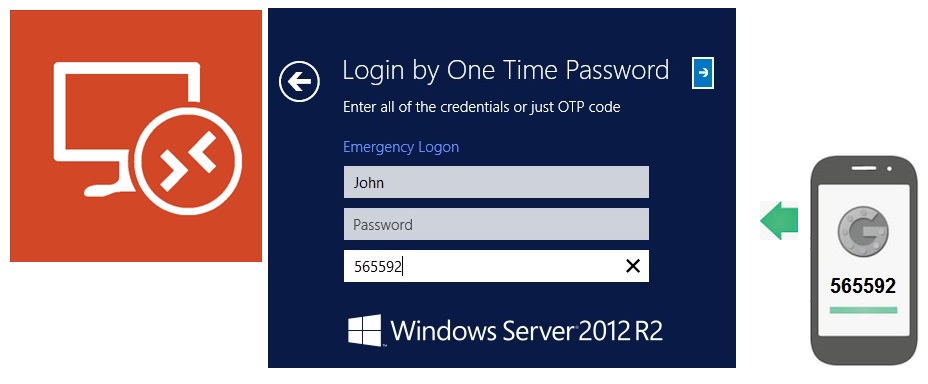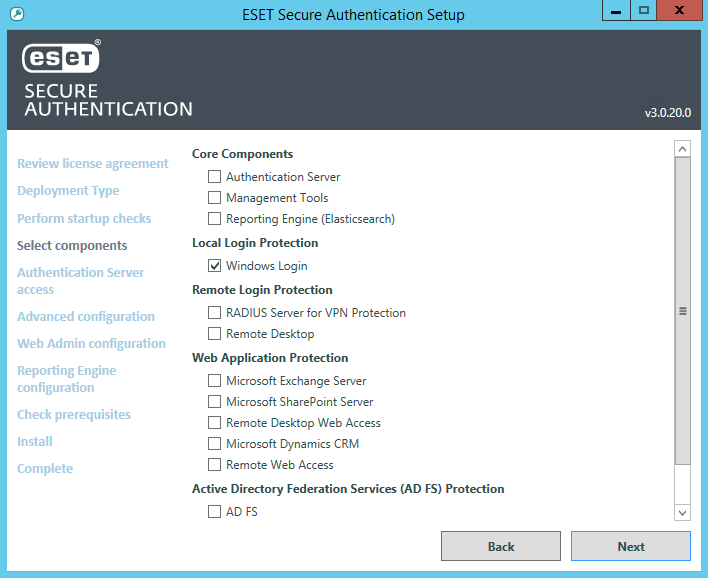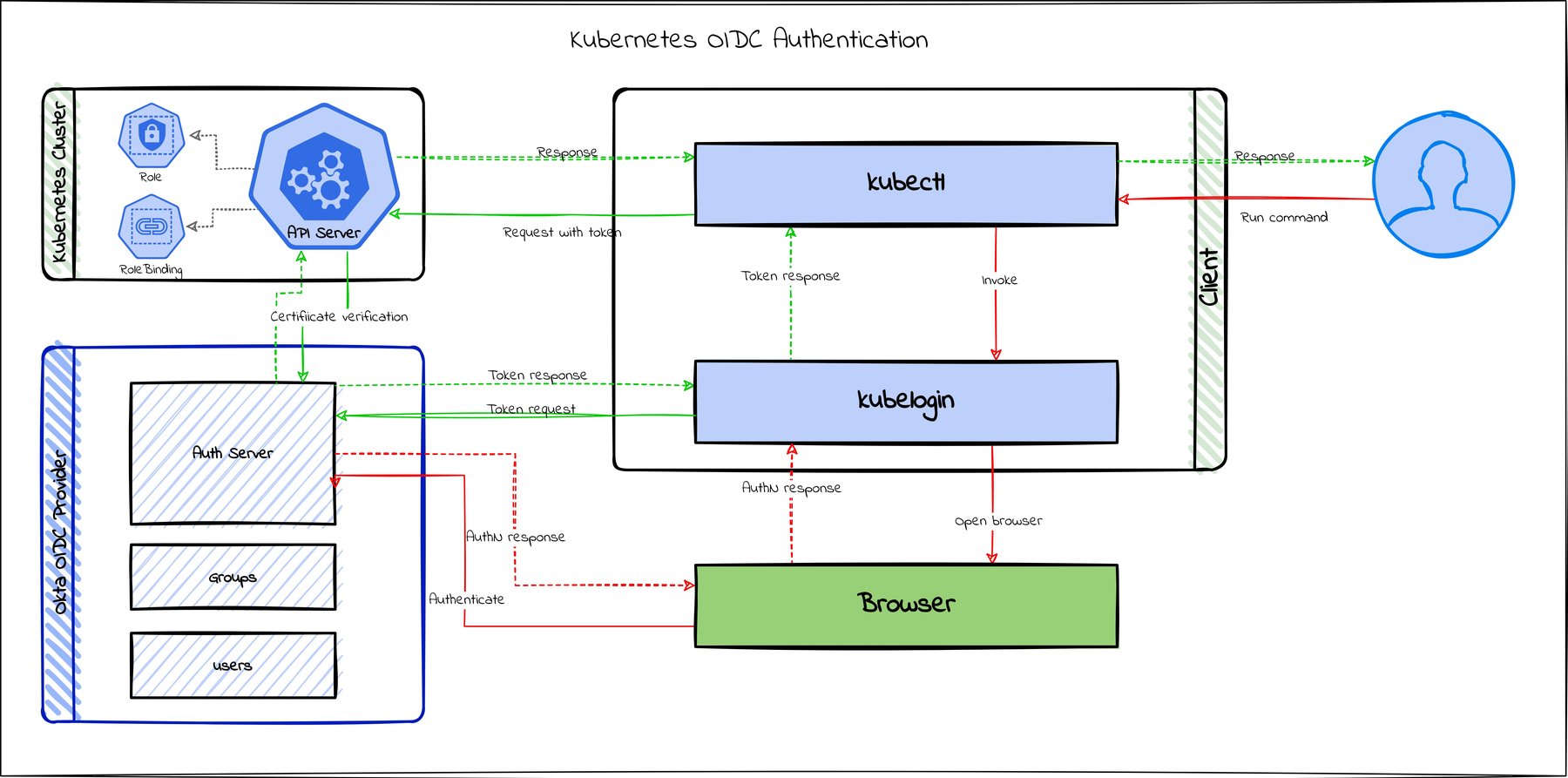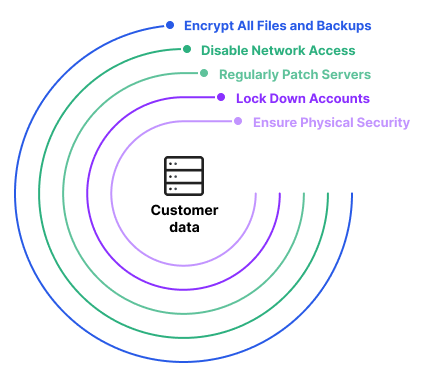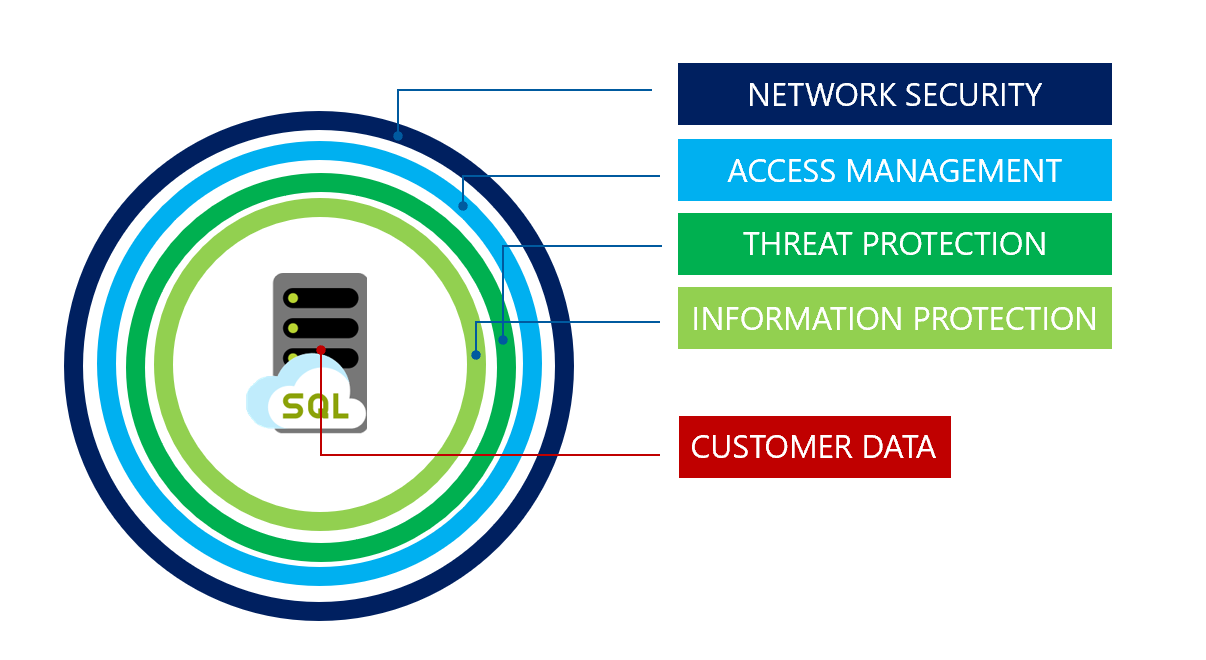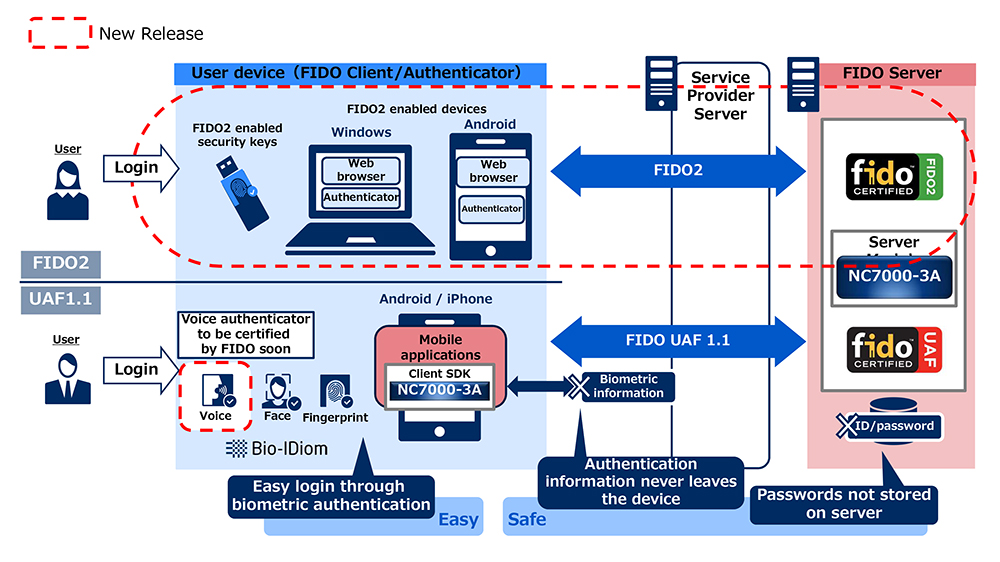
NEC server software enables advanced and secure login to websites in compliance with FIDO2: Press Releases | NEC
Schedule emails in your europe.secureserver.net email account to ensure on-time message delivery February 2023

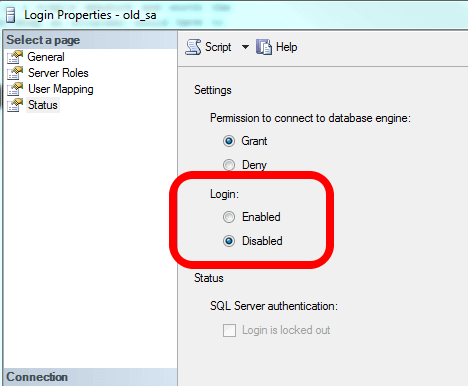
How to secure server services (control panel login/webmail/WHM) with your certificates – HelpDesk | SSLs.com

Cloud Security, Cloud Computing, Data Protecting, Secure Data Exchange. Monitor Screen with Sign Form, Login and Password, Server, Stock Vector - Illustration of connection, exchange: 139858113