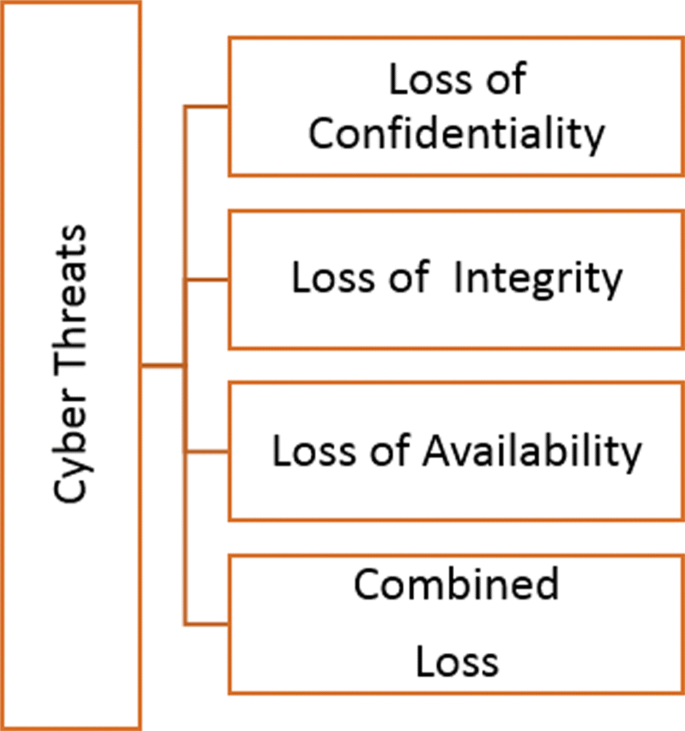
Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
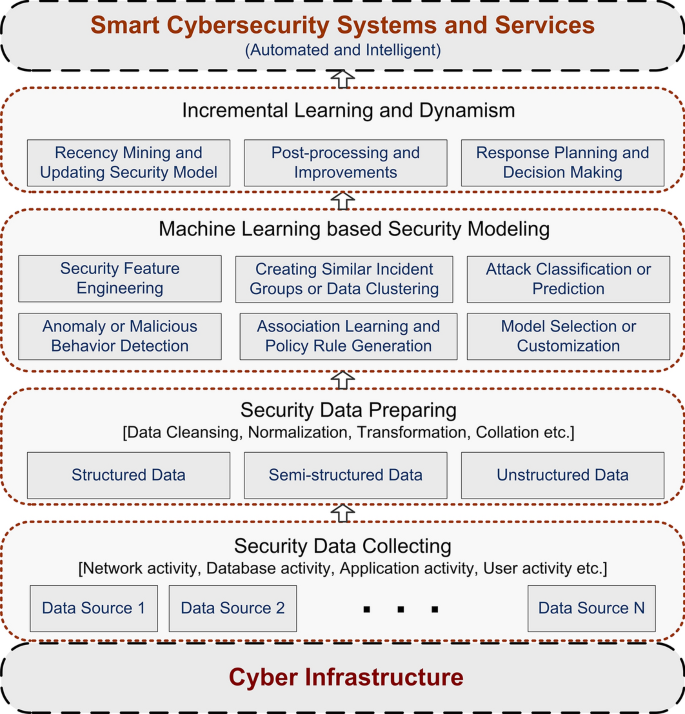
Cybersecurity data science: an overview from machine learning perspective | Journal of Big Data | Full Text
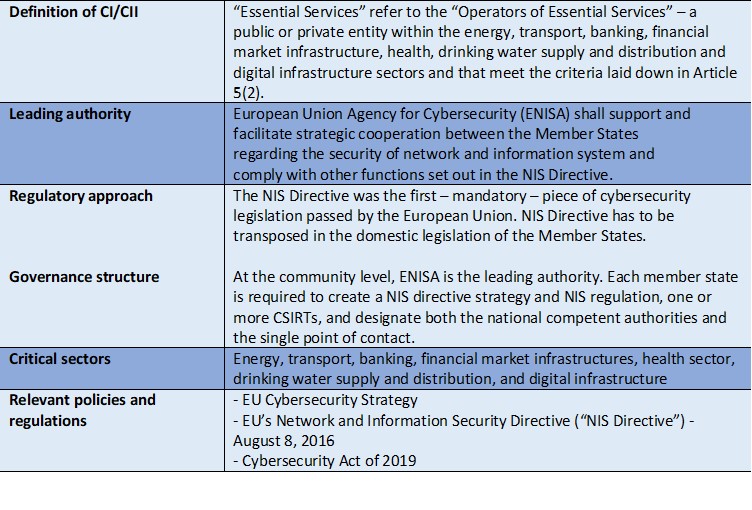
Enhancing the protection and cyber-resilience of critical information infrastructure | Digital Regulation Platform

Understanding the Importance of the Turkish Information and Communication Security Guide on Cybersecurity







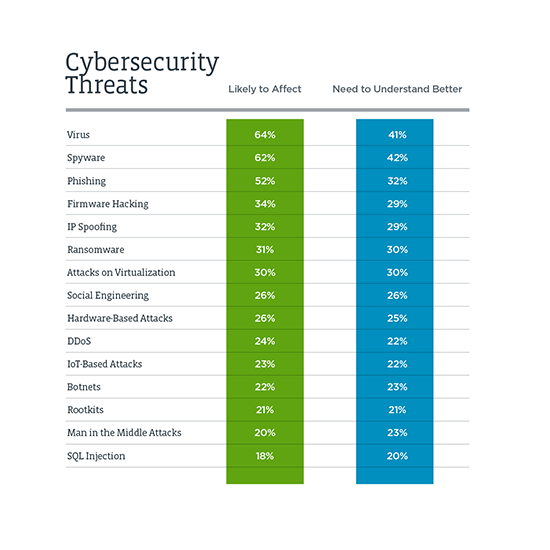
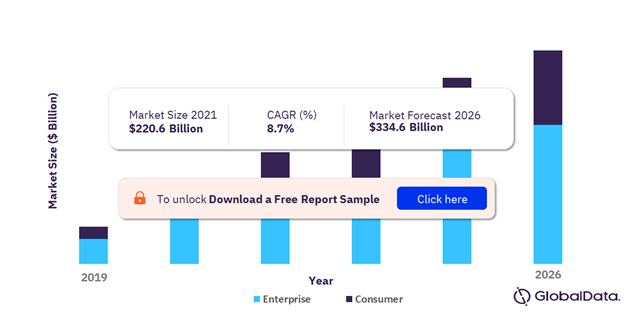
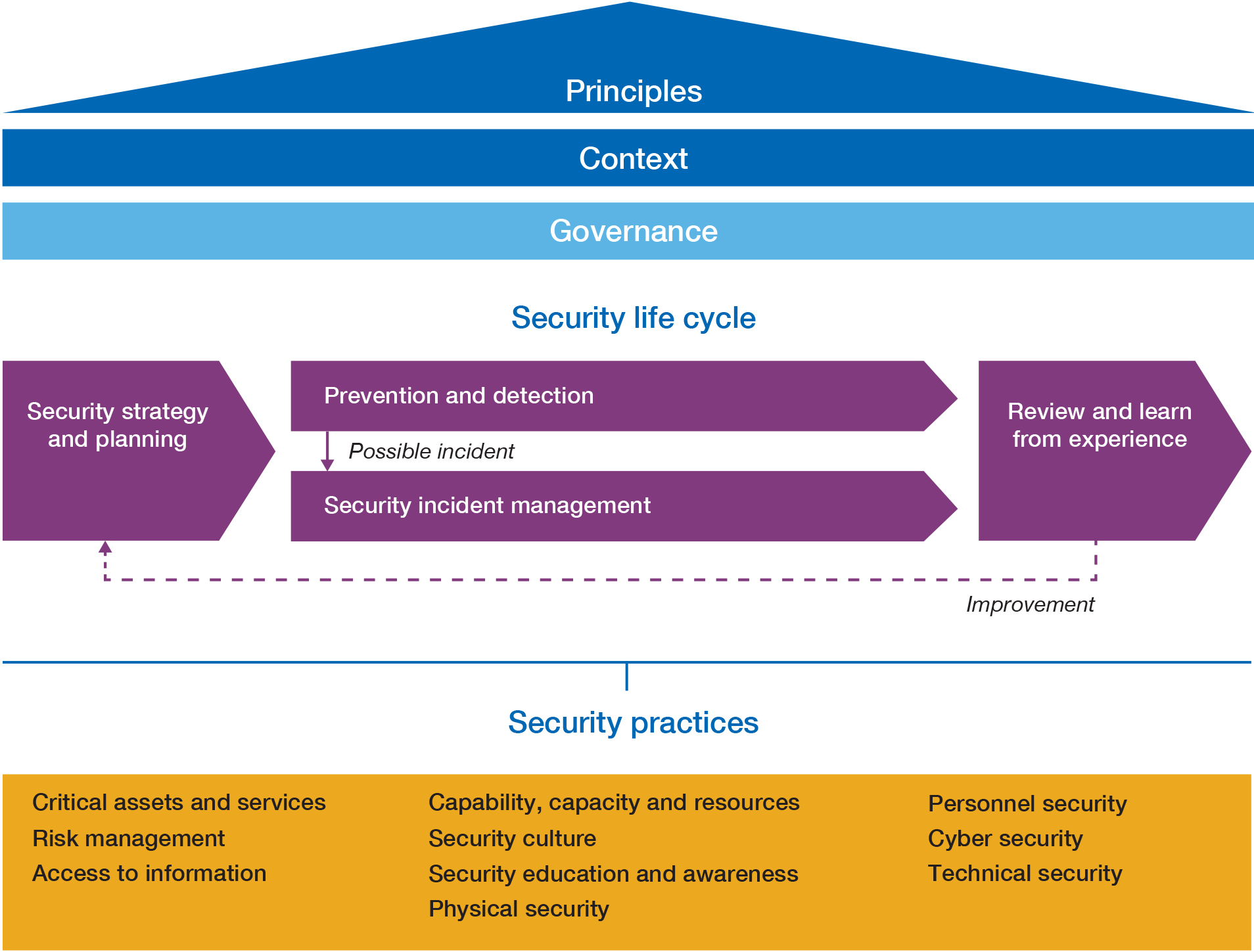

![2 Cyber security CV examples | Analyst | Consultant [Get the job] 2 Cyber security CV examples | Analyst | Consultant [Get the job]](https://cdn.shopify.com/s/files/1/0453/4797/files/Cyber_Security_CV_-_Analyst_1.png?v=1603393275)