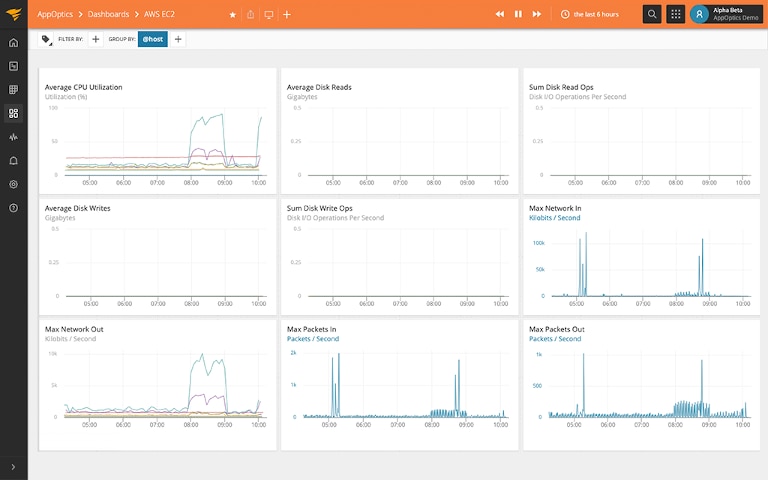
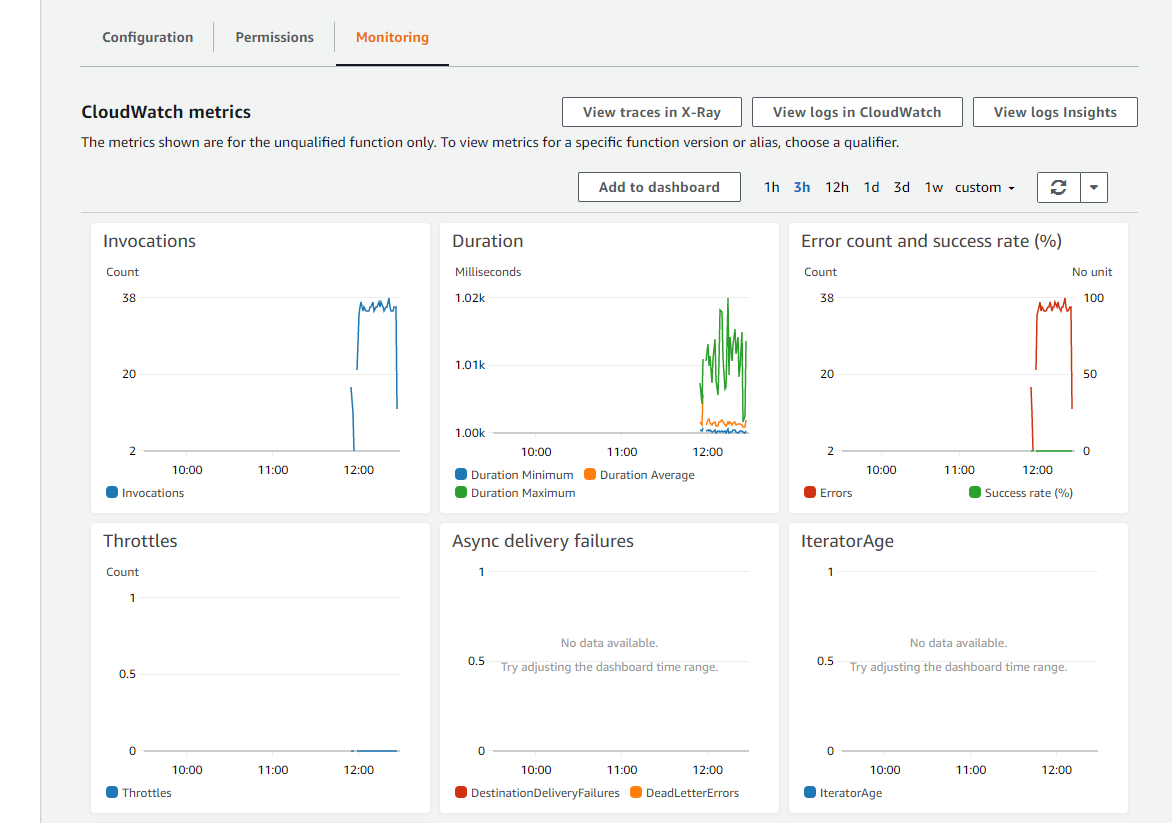
Alarms, incident management, and remediation in the cloud with Amazon CloudWatch | AWS Cloud Operations & Migrations Blog

How to Monitor Host-Based Intrusion Detection System Alerts on Amazon EC2 Instances | AWS Security Blog

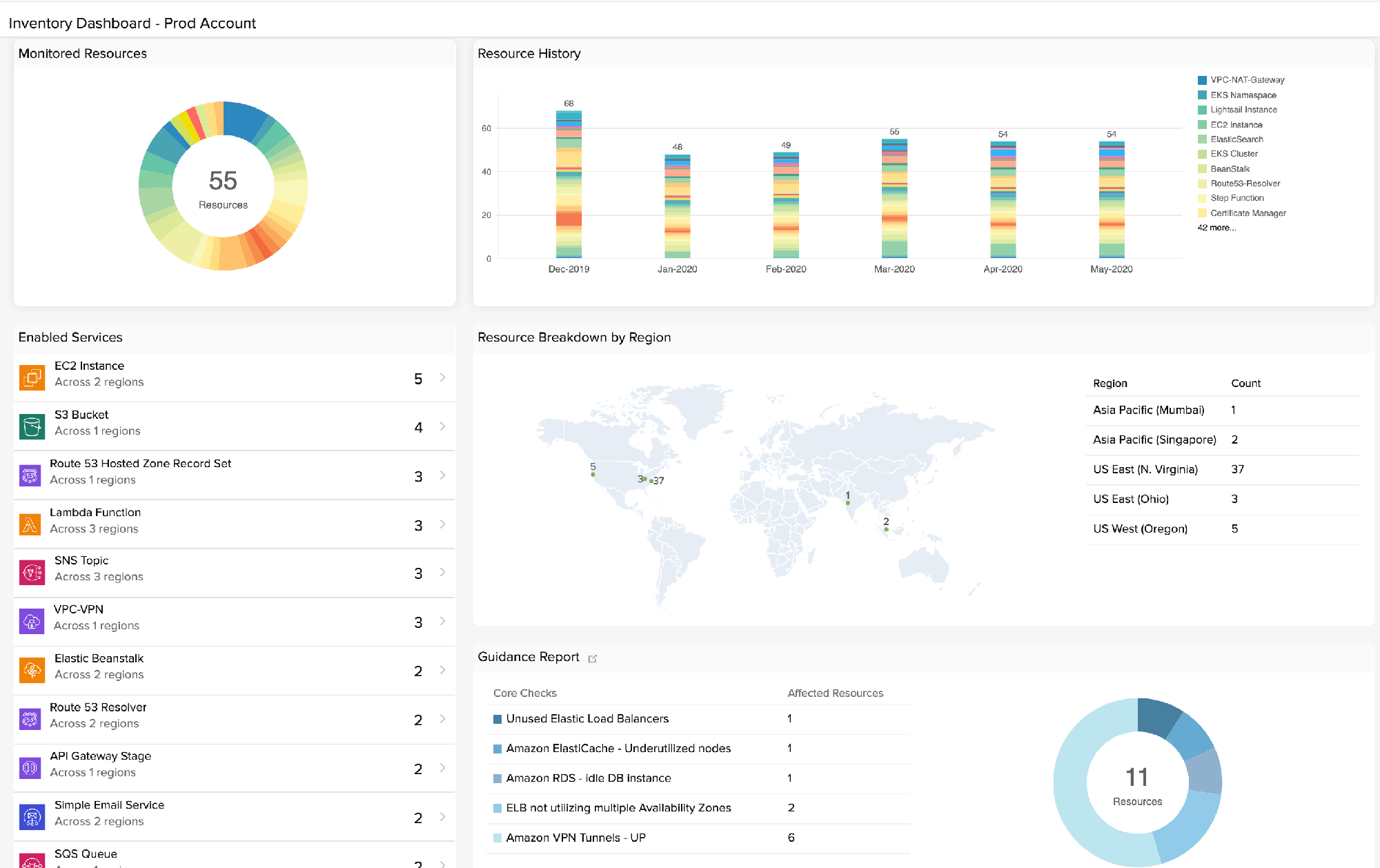
How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Allowing Public Access | AWS Security Blog

How to Monitor and Visualize Failed SSH Access Attempts to Amazon EC2 Linux Instances | AWS Security Blog

Configure logging and monitoring for security events in your AWS IoT environment - AWS Prescriptive Guidance






![AWS IAM: Best practices [Part 1] – DEVOPS DONE RIGHT AWS IAM: Best practices [Part 1] – DEVOPS DONE RIGHT](https://blog2opstree.files.wordpress.com/2021/03/image-36.png)