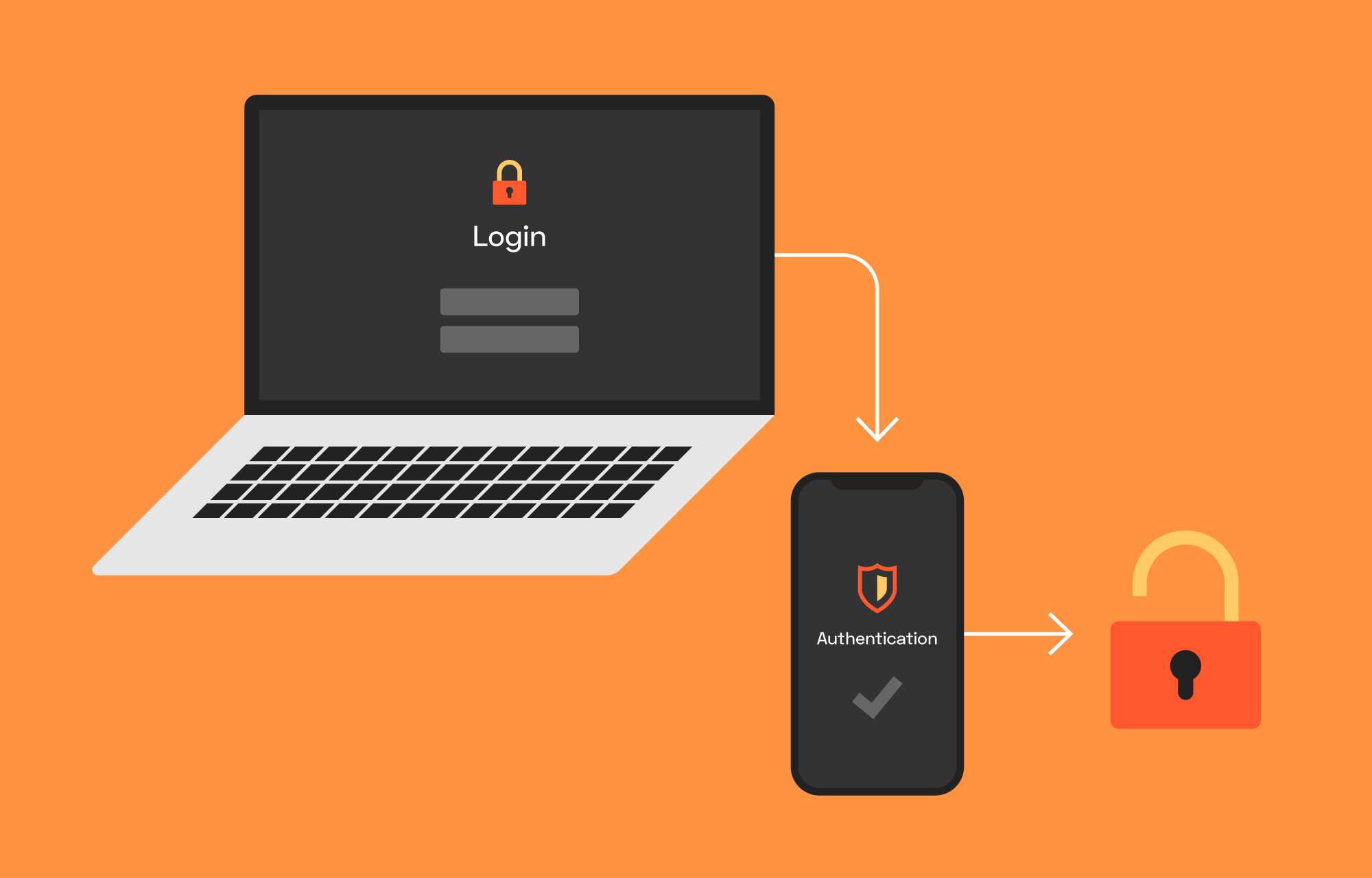
Premium Photo | Two factor authentication or 2fa concept safety shield icon while access on phone with laptop for validate password identity verification cybersecurity with biometrics authentication technology

Two-step authentication and verification online internet account login concept. Casual adult caucasian freelancer man is using smartphone and laptop c Stock Photo - Alamy

Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey | Kaspersky official blog





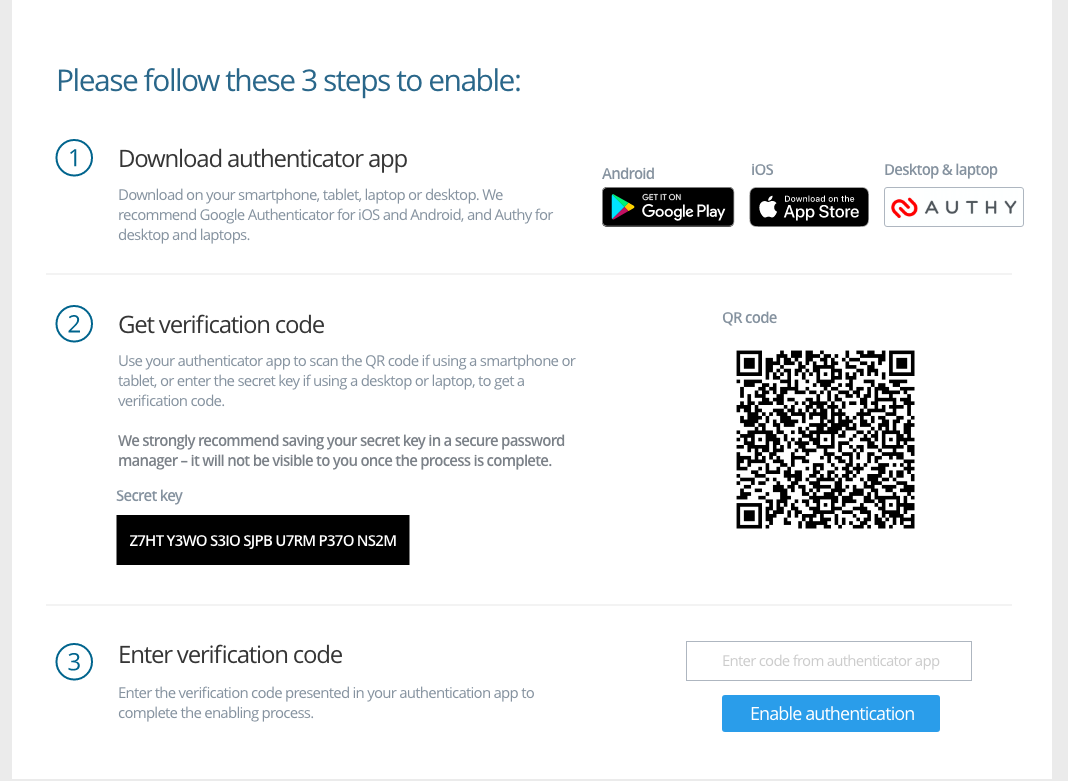
![Duo Security Overview | University Technology, [U]Tech | Case Western Reserve University Duo Security Overview | University Technology, [U]Tech | Case Western Reserve University](https://case.edu/utech/sites/case.edu.utech/files/2018-05/how-it-works_2x.png)
![Is it OK to use text messages for 2-factor authentication? [Ask ZDNet] | ZDNET Is it OK to use text messages for 2-factor authentication? [Ask ZDNet] | ZDNET](https://www.zdnet.com/a/img/resize/d98bbe8f0d4626a2b97edc9de73482a10e73b7b5/2022/03/31/bdec141b-ec57-4272-a201-b74bf3618de0/gettyimages-1311125874-2fa-text2two-steps-authentication-verification-code-message-on-smartphone.jpg?auto=webp&fit=crop&height=900&width=1200)